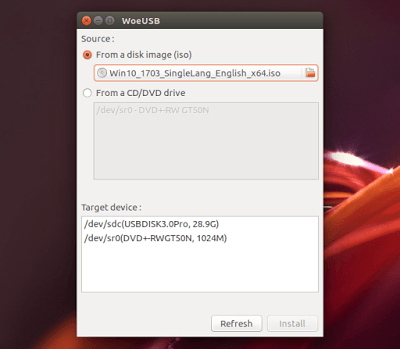
- July 12, 2017Introduction This guide will show you how to download and install Ubuntu Linux on Windows 10 in such a way…
- July 10, 2017Objective Install Firejail and use it to sandbox applications, like web browsers, that interact with the open Internet. Distributions This…
- May 10, 2017Speeding up your Linux Mint is fun! That way, you'll get more performance out of your computer for free. Note: are…